What are the principles used in defining the OSI Layer?
The principles that were applied to arrive at the seven layers were laid down by Day and Zimmermann in 1983, are as follows -
(i) Each layer should perform a well-defined function. (ii) A layer should be created where a different level of abstraction is required.
(iii) The function of each layer should be selected with an eye toward defining internationally standardized protocols. (iv) The layer boundaries should be selected to minimize the information flow across the interfaces.
(v) The number of layers should be large enough that distinct functions need not be thrown together in the same layer out of necessity and small enough that the architecture does not become unwieldy.
(vi) Allow changes in functions of protocols to be made within a layer without affecting other layers.
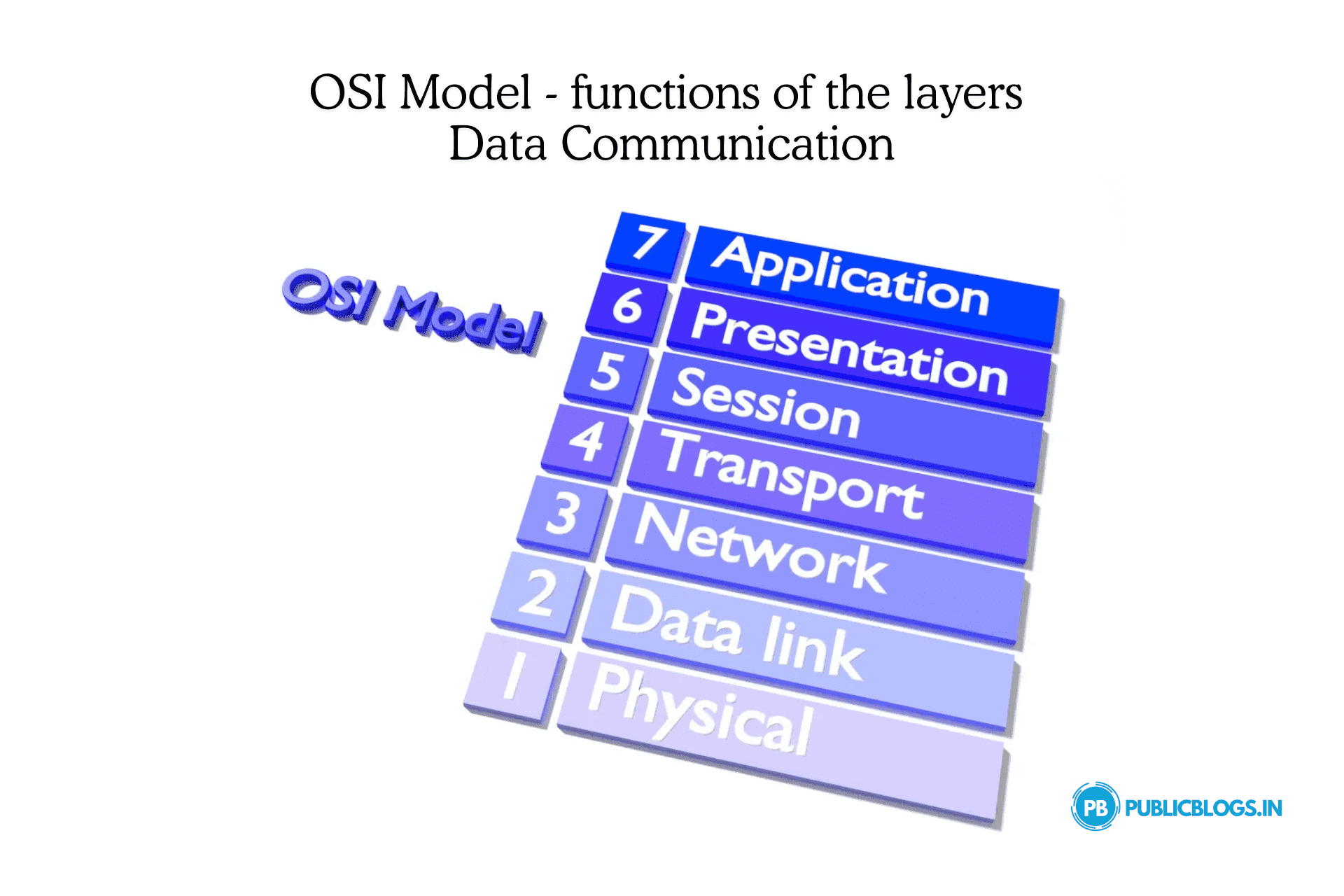
Different Layers in the OSI Model -
International Standards Organization (ISO) in 1983, developed this model as a first step toward international standardization of the protocols used in the various layers. As it deals with connecting open systems, that is, systems that are open for communication with other systems, the model is called the ISO-OSI (Open System Interconnection) Reference Model.
OSI is a layered framework for the design of network systems that permit communication across all types of computer systems. It has seven separate but related layers, each of which defines a segment of the process of moving information across a network.
The OSI model is shown in Fig. The OSI model has seven layers. These are -

The functions of each layer are given as follows -
(i) Physical Layer - This layer coordinates the functions needed to send a bit stream over a physical medium. It deals with the electrical and mechanical specifications of the interface and transmission medium. It also expresses the procedures and functions that physical devices and interfaces have to perform for transmission to take place. The physical layer is related to the following
(a) Representation of Bits- Physical layer data have a stream of bits (sequence of Os and 1s) without any interpretation. For transmission, bits should be encoded into signals-electrical or optical. The type of encoding is defined by the physical layer.
(b) Synchronization of Bits- At the bit level, the transmitter and receiver should be synchronized. In another way, transmitter and receiver clocks should be synchronized.
(c) Transmission Mode-The direction of transmission between two devices - simplex, half-duplex, or full-duplex defined by the physical layer. Simplex mode is a one-way communication in which one device can only send and other can only receive. In the case of half-duplex mode, two devices can send and receive but not at the same time. For two devices sending and receiving at the same time, a full duplex (or simply duplex) mode is used.
(d) Physical Characteristics of Interfaces and Media - The characteristics of the interface between the devices and transmission medium are defined by the physical layer. The physical layer also defines the type of transmission medium.
(e) Data Rate- The physical layer also defines the number of bits: sent each second which is known as the transmission rate. In other words, the duration of a bit is defined by the physical layer, that is how long it lasts.
(f) Physical Topology - The physical topology defines the connection of devices to make a network. Devices can be attached by using a star topology (devices are connected through a central device), a ring topology (each device is attached to the next, making a ring), a mesh topology (each device is connected to every other device), or a bus topology (each device on a common link).
(g) Line Configuration - The physical layer is related to the connection of devices to the medium. In the case of point-to-point configuration, two devices are connected together by a dedicated link. In the multipoint configuration, a link is shared between many devices.
(ii) Data Link Layer - The physical layer is transformed by the data link layer, a raw transmission facility, to a reliable link and is responsible for node-to-node delivery. It makes the physical layer appear error-free to the
upper layer. The main functions of the data link layer are the following-
(a) Framing- The data link layer divides the bits stream received from the network layer into manageable data units known as frames.
(b) Physical Addressing - The data link layer adds a header to the frame to define the physical address of the transmitter (source address) and receiver (destination address) of the frame when frames are to be distributed to various systems on the network. The receiver address is the address of the device that connects one network to the next when the frame is intended for a system outside the sender's network.
(c) Flow Control- When the rate at which the data are absorbed by the receiver is less than the rate generated in the transmitter, the data link layer imposes a flow control mechanism to prevent overwhelming the receiver.
(d) Error Control - By adding mechanisms to detect and retransmit damaged or lost frames, the data link layer adds reliability to the physical layer. It also employs a mechanism to prevent duplication of frames. Generally, error control is obtained via a trailer added to the frame end.
(e) Access Control - Data link layer protocols are required to decide which device has control over the link at any given time if two or more devices are connected to the same link.
(iii) Network Layer-The network layer is responsible for the source-to-destination delivery of a packet across multiple networks (links). required to There is no need for a network layer when two systems are connected to the same link. However, there is a requirement for a network to achieve source-to-destination delivery when two systems are connected to several networks (link) with connecting devices among the networks (links). Specific functions of the network layer include the following-
(a) Routing - If independent networks or links are attached together to develop an internetwork (a network of networks) or a large network the connecting devices (known as routers or gateways) route the packets to their final destination.
(b) Logical Addressing - The addressing problem is locally handled by the physical addressing implemented by the data link layer. Another addressing system is required to help distinguish the source and destination systems when a packet passes the network boundary. A header is added by the network layer to the packet coming from the upper layer that, among other things, includes the logical addresses of the transmitter and receiver.
(iv) Transport Layer - For source-to-destination (end-to-end) delivery of the entire message, the transport layer is responsible. While the network layer oversees the end-to-end delivery of individual packets, it does not recognize any relationship between those packets. In other words, the transport layer ensures that the entire message arrives intact and in order, overseeing both flow control and error control at the source-to-destination level.
Specific functions of the transport layer include the following-
(a) Segmentation and Reassembly - The message is split into transmittable segments, every segment having a sequence number. These numbers enable the transport layer to reassemble the message accurately upon arriving at the destination and to identify and replace packets that were lost in the transmission.
(b) Error Control - Similar to the data link layer, the transport layer is responsible for error control. However, at this layer, error control is done end-to-end rather than across a single link. The sending transport layer ensures that the whole message arrives at the receiving transport layer without error. Usually, error correction is obtained through retransmission.
(c) Service-point Addressing - Computers often run many programs at the same time. Due to this reason, source-to-destination delivery means delivery not only from one computer to the next but also from a specific process (running program) on one computer to a specific process (running program) on the other. Therefore, the transport layer header must include a type of address known as a service-point address (or port address). Each packet is received by the network layer to the correct computer. The complete message is received by the transport layer, to the correct process on that computer.
(d) Flow Control- Similar to the data link layer, the transport layer is responsible for flow control. But, at this layer, flow control is done end to end rather than across a single link. (e) Connection Control - This layer can be either connection-oriented or connectionless. A connectionless transport layer deals with each segment like an independent packet and delivers it to the transport layer at the destination machine. A connection is established by a connection-oriented transport layer with the transport layer at the destination machine first before delivering the packets. The connection is terminated after all the data are transferred.
(v) Session Layer-The session layer is the network dialog controller. It establishes, maintains, and synchronizes the interaction between communicating systems. Specific functions of the session layer include the following-
(a) Synchronization - This layer permits a process to add checkpoints (synchronization points) into a data stream. For example, at the time of sending a file of 2000 pages by a system, it is advisable to insert a checkpoint after every 100 pages to make sure that each 100-page unit is received and acknowledged independently.
(b) Dialog Control- This layer permits two systems to enter into a dialog. It permits the communication between two processes to occur either in half-duplex (one way at a time) or full-duplex (two ways at a time).
(vi) Presentation Layer- The function of the presentation layer is to ensure that communicating machines can interoperate properly. For application programs to understand the information transferred between devices that have different internal data representations, a common syntax must be used. This syntax represents information such as character codes, data types, and file formats. Hence, the presentation layer protocols determine what syntax to use when applications in different machines exchange information. The presentation layer has the following specific responsibilities -
(a) Encryption - A system must be able to assure privacy for carrying sensitive information. Encryption means that the transmitter transforms the original information into another form and transmits the resulting message out over the network. The original process is reversed by the decryption to transform the message back to its original form.
(b) Translation - Usually, the processes (running programs) in two systems exchange information in the form of character strings, numbers, and so on. Before being transmitted, the information should be converted to bit streams. The presentation layer is responsible for interoperability between these different encoding methods because different computers use different encoding systems. At the transmitter, the presentation layer converts the information from its sender-dependent format into a common format. At the receiving machine, the presentation layer converts the common format into its receiver-dependent format.
(c) Compression - Data compression minimizes the number of bits to be sent. Data compression is particularly important in the transmission of multimedia such as text, audio, and video.
(vii) Application Layer - The application layer enables the user to access the network. It gives user interfaces and support for services such as electronic mail, remote file access and transfer, etc. The following specific services are provided by the application layer-
(a) File Transfer, Access, and Management (FTAM) - This application permits a user to access files in a remote computer (to make changes or read data), retrieve files from a remote computer, and manage or control files in a remote computer.
(b) Network Virtual Terminal - This is a software version of a physical terminal and permits a user to log on to a remote host. To do so, the application develops a software emulation of a terminal at the remote host. The user's computer talks to the software terminal, which in turn, talks to the host, and vice versa.
(c) Directory Services - Distributed database sources and access to global information about different objects and services are provided by this application.
(d) Mail Services-The basis for e-mail forwarding and storage are provided by this application.
Do you dream of turning your thoughts and words into income ? join us now and become blogger now.

0 Comments
Leave a Comment